DevSecOps Services That Fit Your Product By NextGenSoft
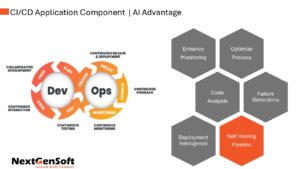
Most teams don’t fail because of bad code. They fail because security comes in too late. Our services embed security into your architecture, pipelines, and cloud environments from the start. Issues are caught early, not during release week.
We begin by reviewing how your product is built and deployed today. Our DevSecOps consulting services design secure CI/CD pipelines and automated security checks. Every build and deployment follows the same rules, without manual intervention.
This removes release risk and reduces production failures. Teams move faster without cutting corners. With our DevSecOps managed services, security becomes part of delivery, not a blocker to it.

Why Security is Essential in DevSecOps?
Early Risk Detection
Now identify and fix security during development, not after the release. With DevOpsSec Services, automated scanning and continuous testing catch the issue early, while it is still easy to fix.
Predictable Release Cycles
When deployments depend on manual steps and scattered tools, every release is risky. DevSecOps Services bring consistency, same checks, same controls, same outcome, so you know exactly what’s going live.
Faster Time to Market
Security shouldn’t slow engineers down or sit on their shoulders. DevSecOps Services automate enforcement so teams can focus on building, not double-guessing every commit.
Built-In Compliance
Instead of scrambling for audits or evidence, controls are already in place. DevSecOps Services make compliance continuous and repeatable, not something you “prepare for.”
End-to-End Delivery Visibility
You can trace changes, from code to deployment to runtime, without piecing things together. That clarity alone saves hours during incidents and reviews.
Lower Operational Costs
Security flaws and environmental issues are cheapest when caught early. This service reduce rework, emergency patches, and long-term operational drag. Especially when supported through structured DevSecOps managed services rather than ad-hoc security fixes.
Challenges in DevSecOps
However, it is crucial to establish an efficienct and versatile DevSecOps strategy, but this may affect the seamless implementation and workflow of the organization.
Security Delays Releases at the Final Stage
When security is added at the end, issues surface right before release. Teams either delay launches or push risky code into production, both of which hurt the business.
Automation Fails to Improve Delivery Speed
CI/CD alone doesn’t fix everything. Without DevSecOps, pipelines move fast until security reviews stop them, creating bottlenecks no one planned for.
Operational Incidents Become More Frequent
Hidden vulnerabilities make it into production. Over time, this leads to frequent patches, hotfixes, and unplanned downtime that drains engineering focus.
Compliance Relies on Manual Effort
Audits and compliance checks rely on documents and manual reviews. This increases effort, errors, and stress, especially as the product scales.
Delivery Teams Remain Disconnected
Development ships features, security flags, risks, and operations deal with failures. Without DevSecOps, no one owns the full delivery lifecycle.
Scaling the Product Becomes Risky
As traffic, data, and users grow, security gaps grow with them. What worked early starts breaking under real-world load and threats.
Security and Operations Costs Escalate
Fixing security issues after release is expensive. Teams spend more time on rework, incident response, and support instead of building new features.
Release Confidence Declines Over Time
Over time, teams lose trust in deployments. Every release feels risky, which slows decision-making and limits how fast the business can move.
The DevSecOps Standards We Follow
Process Before Automation
If your release process is messy, automating it just makes the mess faster. We first clean up how code moves from commit to production, then add security and automation where it makes sense.
Security Built Into Development
Security shouldn’t show up at the end and block a launch. We plug it into code commits, builds, and infrastructure changes so issues surface early, when they’re easier to fix.
Stable, Predictable Pipelines
Over-engineered pipelines fail under pressure. We design CI/CD pipelines that are easy to understand, easy to debug, and reliable during high-stakes releases.
Risk-Based Tool Selection
Every product has different risks. We select security and DevSecOps tools based on what your system actually needs, not what’s trending or overkill.
Resilient Release Design
Things break in real environments; that’s normal. We plan rollbacks, alerts, and recovery paths upfront so a bad release doesn’t turn into a business incident.
Long-Term Team Ownership
DevSecOps only works if your team understands it. We document decisions, explain why things are built a certain way, and make sure you’re not dependent on us after delivery.
Why NextGenSoft?
End-to-End Expertise
Partner with NextGenSoft, a global digital transformation company, and leverage our multi-cloud engineers’ abilities. As a trusted IT solutions provider, we build up secure inter-cloud networks, map native cloud services, and make vendor-agnostic methodologies to maximize esteem and minimize dangers.
Delivery Excellence
We rethink delivery excellence with optimized program lifecycles. From development to deployment, our digital transformation services and solutions ensure reliable, high-quality releases that enhance client satisfaction, as showcased in our Case Studies.
Flexible Hiring Model
NextGenSoft’s adaptable contracting models give access to talented IT service providers custom-fitted to your needs. Scale easily with agile assets for DevOps, guaranteeing consistent collaboration and venture victory.
Transparent Actions
Our commitment to straightforwardness builds belief and cultivates cooperation. As a leading digital transformation company in India, we ensure adjusted objectives, open communication, and compelling collaboration for shared success.
Security Tools
- SAST Tools
- DAST Tools
- SCA Tools
- IaC Security Tools
- SIEM Tools
- Secret Management Tools
- Pipeline Security Tools
- EDR Tools
- Threat Intelligence Tools
- CSPM Tools
- IAM Tools
Static Application Security Testing (SAST) Tools
Dynamic Application Security Testing (DAST) Tools
OWASP ZAP (Zed Attack Proxy)
Burp Suite
Acunetix
Software Composition Analysis (SCA) Tools
Snyk
WhiteSource
OSS Index
IaC Security Tools
Terraform
Checkov
TFSec
Security Information and Event Management (SIEM) Tools
Splunk
Elastic Stack (ELK)
Sumo Logic
Secret Management Tools
Vault (HashiCorp)
AWS Secrets Manager
Azure Key Valut
CyberArk Conjur
Google Cloud Secret Manager
Pipeline Security Tools
OWASP Dependency-Check
JFrog Xray
SonarQube
Snyk
Trivy
KICS
EDR (Endpoint Detection and Response) Tools
Carbon Black
Microsoft Defender for Endpoint
Trend Micro Apex One
Threat Intelligence Tools
MISP
ThreatConnect
Recorded Future
CSPM (Cloud Security Posture Management) Tools
Prisma Cloud (Palo Alto Networks)
Wiz
Lacework
Bridgecrew
IAM (Identity and Access Management) Tools
Okta
AWS IAM
Auth0
Azure Active Directory (Azure AD)
Our Security Implementation Strategy
Assess Your Current Delivery Workflow
We review your code flow, deployment process, cloud setup, and past production issues. This helps us identify where security slows you down or breaks things later. This is often where DevSecOps consulting services create the biggest impact.
Embed Security Directly Into Delivery
We integrate automated security testing directly into the CI/CD pipeline. So, problems are caught early, not right before release.
Automate Infrastructure and Security Controls
Infrastructure, configurations, and access rules are managed as code. This removes guesswork, reduces human error, and keeps environments consistent.
Monitor and Protect in Production
We also include Real-time monitoring and alerts to give you continuous visibility of your production environment. It’ll catch risks, misconfigurations, and any unusual behavior before it goes live.
Optimize Continuously as You Grow
As your product and traffic grow, we fine-tune pipelines, controls, and processes so DevSecOps continues to support speed, not block it.
Blogs
Browse through the technical knowledge about latest trends and technologies our experienced team would like to share with you.
View all articlesAI and ML in CI/CD: The Rise of Intelligent Pipelines
Let's dive into how AI and machine learning are changing the game for CI/CD. It's not just about automation anymore; we're talking about intelligent automation that's making software development faster, smoother, and more reliable.
Architecting for Success: Essential System Design Principles for Developers
In the IT industry, it is a common yet critical mistake to dive straight into coding when starting a new project. However, this approach can lead to inefficiencies, technical debt, and costly rework down the line.
Mastering Power BI Embedding: A Comprehensive Guide for Developers
In today's data-driven world, the ability to visualize data effectively is more critical than ever. Power BI, a powerful business analytics tool from Microsoft, allows users to create interactive and insightful reports and dashboards.
Enhance Security with other DevOps Services

CI/CD Services
CI/CD Services automate builds, tests, and security checks so every release moves fast without cutting corners or relying on manual approvals.

Cloud DevOps Services
Cloud DevOps Services create stable, secure cloud environments that support DevSecOps Services as systems scale and change.

Containerization Services
Containerization Services keep applications predictable across development, staging, and production while enforcing security standards consistently.

DevOps Assessment
A DevOps Assessment shows where DevSecOps Services are slowing down, breaking, or being bypassed, and what needs fixing to restore control.
Frequently Asked Questions
-
Will DevSecOps break our current delivery process?
No. We don’t rip things apart. We study how your team already builds and releases software, then layer security into that flow so it feels natural, not forced. -
How early do you introduce security checks?
Right from the first commit. We shift security left so issues are caught while code is being written, not days before release when fixes are expensive and stressful. -
What security tasks do you automate first?
The ones slowing you down today are code scans, dependency checks, secrets detection, and container scanning. Manual reviews are replaced with reliable automation that runs every time. -
Can this work with our cloud and Kubernetes setup?
Yes. Our DevSecOps implementation services are designed specifically for cloud, containers, and Kubernetes environments. Security policies follow your workloads, no matter where or how they run. -
How is NextGenSoft’s DevSecOps approach different?
We don't sell tools or templates; we engineer outcomes. NextGenSoft's DevSecOps implementation services embed security based on how your teams actually work. To make sure DevSecOps drives speed, stability, and business confidence, not process overhead. -
What happens after DevSecOps goes live?
We keep watching and improving. As your product grows, we refine policies, update tools, and adapt controls so security scales with you, not against you. -
How do you align DevSecOps with compliance requirements?
We translate compliance into enforceable policies inside pipelines. This ensures controls are always active, evidence is continuously generated, and audits stop being disruptive events.



































 Pranav Lakhani
Pranav Lakhani 
 Niraj Salot
Niraj Salot 
 Kushal Baldev
Kushal Baldev